프로세스의 주요 구조체
- EPROCESS
- KPROCESS
- PEB(Process Environment Block)
- HANDLE
- OBJECT
- TOKEN
1. !process extension
위 프로세스 관련 주요 구조체에 대해서 notepad.exe 프로세스를 이용하여, 살펴보도록 하겠습니다.
Windbg에서는 프로세스 관련 내용을 살펴보기 위해서 가장 많이 사용되는 extension으로 !process를 이용합니다.
우선 !process를 이용하여, notepad.exe 프로세스에 대해서 다음과 같은 내용을 살펴볼 수 있습니다.
| 3: kd> !process 0 0 notepad.exe PROCESS ffffbc0c19c33080 SessionId: 1 Cid: 0318 Peb: c1e88f0000 ParentCid: 1010 DirBase: 1161d5000 ObjectTable: ffff918d8b13f600 HandleCount: 245. Image: notepad.exe |
PROCESS ffffbc0c19c33080 ## EPROCESS 구조체 주소
Cid: 0318 ## 프로세스 ID
Peb: c1e88f0000 ## Process Environment Block 주소
ParentCid: 1010 ## 부모 프로세스 ID
부모 프로세스 ID 값을 이용하여, notepad.exe 프로세스의 부모 프로세스가 explorer.exe 인 것을 확인
| 2: kd> !process 1010 0 Searching for Process with Cid == 1010 PROCESS ffffbc0c19c3d080 SessionId: 1 Cid: 1010 Peb: 00d54000 ParentCid: 048c DirBase: 103eb4000 ObjectTable: ffff918d8a010d40 HandleCount: 1513. Image: explorer.exe |
Image: notepad.exe ## EProcess.ImageFileName 값을 출력
| 2: kd> dt nt!_EPROCESS ffffbc0c19c33080 ImageFileName +0x450 ImageFileName : [15] "notepad.exe" |
2. EPROCESS 구조체
EPROCESS 구조체에는 KPROCESS, PEB, HANDLE_TABLE 등 다른 주요 구조체에 대한 포인터 위치를 가지고 있습니다.
3: kd> dt nt!_EPROCESS
+0x000 Pcb : _KPROCESS
+0x2d8 ProcessLock : _EX_PUSH_LOCK
+0x2e0 UniqueProcessId : Ptr64 Void
+0x2e8 ActiveProcessLinks : _LIST_ENTRY
+0x2f8 RundownProtect : _EX_RUNDOWN_REF
+0x300 Flags2 : Uint4B
+0x300 JobNotReallyActive : Pos 0, 1 Bit
+0x300 AccountingFolded : Pos 1, 1 Bit
+0x300 NewProcessReported : Pos 2, 1 Bit
+0x300 ExitProcessReported : Pos 3, 1 Bit
+0x300 ReportCommitChanges : Pos 4, 1 Bit
+0x300 LastReportMemory : Pos 5, 1 Bit
+0x300 ForceWakeCharge : Pos 6, 1 Bit
+0x300 CrossSessionCreate : Pos 7, 1 Bit
+0x300 NeedsHandleRundown : Pos 8, 1 Bit
+0x300 RefTraceEnabled : Pos 9, 1 Bit
+0x300 PicoCreated : Pos 10, 1 Bit
+0x300 EmptyJobEvaluated : Pos 11, 1 Bit
+0x300 DefaultPagePriority : Pos 12, 3 Bits
+0x300 PrimaryTokenFrozen : Pos 15, 1 Bit
+0x300 ProcessVerifierTarget : Pos 16, 1 Bit
+0x300 RestrictSetThreadContext : Pos 17, 1 Bit
+0x300 AffinityPermanent : Pos 18, 1 Bit
+0x300 AffinityUpdateEnable : Pos 19, 1 Bit
+0x300 PropagateNode : Pos 20, 1 Bit
+0x300 ExplicitAffinity : Pos 21, 1 Bit
+0x300 ProcessExecutionState : Pos 22, 2 Bits
+0x300 EnableReadVmLogging : Pos 24, 1 Bit
+0x300 EnableWriteVmLogging : Pos 25, 1 Bit
+0x300 FatalAccessTerminationRequested : Pos 26, 1 Bit
+0x300 DisableSystemAllowedCpuSet : Pos 27, 1 Bit
+0x300 ProcessStateChangeRequest : Pos 28, 2 Bits
+0x300 ProcessStateChangeInProgress : Pos 30, 1 Bit
+0x300 InPrivate : Pos 31, 1 Bit
+0x304 Flags : Uint4B
+0x304 CreateReported : Pos 0, 1 Bit
+0x304 NoDebugInherit : Pos 1, 1 Bit
+0x304 ProcessExiting : Pos 2, 1 Bit
+0x304 ProcessDelete : Pos 3, 1 Bit
+0x304 ManageExecutableMemoryWrites : Pos 4, 1 Bit
+0x304 VmDeleted : Pos 5, 1 Bit
+0x304 OutswapEnabled : Pos 6, 1 Bit
+0x304 Outswapped : Pos 7, 1 Bit
+0x304 FailFastOnCommitFail : Pos 8, 1 Bit
+0x304 Wow64VaSpace4Gb : Pos 9, 1 Bit
+0x304 AddressSpaceInitialized : Pos 10, 2 Bits
+0x304 SetTimerResolution : Pos 12, 1 Bit
+0x304 BreakOnTermination : Pos 13, 1 Bit
+0x304 DeprioritizeViews : Pos 14, 1 Bit
+0x304 WriteWatch : Pos 15, 1 Bit
+0x304 ProcessInSession : Pos 16, 1 Bit
+0x304 OverrideAddressSpace : Pos 17, 1 Bit
+0x304 HasAddressSpace : Pos 18, 1 Bit
+0x304 LaunchPrefetched : Pos 19, 1 Bit
+0x304 Background : Pos 20, 1 Bit
+0x304 VmTopDown : Pos 21, 1 Bit
+0x304 ImageNotifyDone : Pos 22, 1 Bit
+0x304 PdeUpdateNeeded : Pos 23, 1 Bit
+0x304 VdmAllowed : Pos 24, 1 Bit
+0x304 ProcessRundown : Pos 25, 1 Bit
+0x304 ProcessInserted : Pos 26, 1 Bit
+0x304 DefaultIoPriority : Pos 27, 3 Bits
+0x304 ProcessSelfDelete : Pos 30, 1 Bit
+0x304 SetTimerResolutionLink : Pos 31, 1 Bit
+0x308 CreateTime : _LARGE_INTEGER
+0x310 ProcessQuotaUsage : [2] Uint8B
+0x320 ProcessQuotaPeak : [2] Uint8B
+0x330 PeakVirtualSize : Uint8B
+0x338 VirtualSize : Uint8B
+0x340 SessionProcessLinks : _LIST_ENTRY
+0x350 ExceptionPortData : Ptr64 Void
+0x350 ExceptionPortValue : Uint8B
+0x350 ExceptionPortState : Pos 0, 3 Bits
+0x358 Token : _EX_FAST_REF
+0x360 MmReserved : Uint8B
+0x368 AddressCreationLock : _EX_PUSH_LOCK
+0x370 PageTableCommitmentLock : _EX_PUSH_LOCK
+0x378 RotateInProgress : Ptr64 _ETHREAD
+0x380 ForkInProgress : Ptr64 _ETHREAD
+0x388 CommitChargeJob : Ptr64 _EJOB
+0x390 CloneRoot : _RTL_AVL_TREE
+0x398 NumberOfPrivatePages : Uint8B
+0x3a0 NumberOfLockedPages : Uint8B
+0x3a8 Win32Process : Ptr64 Void
+0x3b0 Job : Ptr64 _EJOB
+0x3b8 SectionObject : Ptr64 Void
+0x3c0 SectionBaseAddress : Ptr64 Void
+0x3c8 Cookie : Uint4B
+0x3d0 WorkingSetWatch : Ptr64 _PAGEFAULT_HISTORY
+0x3d8 Win32WindowStation : Ptr64 Void
+0x3e0 InheritedFromUniqueProcessId : Ptr64 Void
+0x3e8 Spare0 : Ptr64 Void
+0x3f0 OwnerProcessId : Uint8B
+0x3f8 Peb : Ptr64 _PEB
+0x400 Session : Ptr64 _MM_SESSION_SPACE
+0x408 Spare1 : Ptr64 Void
+0x410 QuotaBlock : Ptr64 _EPROCESS_QUOTA_BLOCK
+0x418 ObjectTable : Ptr64 _HANDLE_TABLE
+0x420 DebugPort : Ptr64 Void
+0x428 WoW64Process : Ptr64 _EWOW64PROCESS
+0x430 DeviceMap : Ptr64 Void
+0x438 EtwDataSource : Ptr64 Void
+0x440 PageDirectoryPte : Uint8B
+0x448 ImageFilePointer : Ptr64 _FILE_OBJECT
+0x450 ImageFileName : [15] UChar
+0x45f PriorityClass : UChar
+0x460 SecurityPort : Ptr64 Void
+0x468 SeAuditProcessCreationInfo : _SE_AUDIT_PROCESS_CREATION_INFO
+0x470 JobLinks : _LIST_ENTRY
+0x480 HighestUserAddress : Ptr64 Void
+0x488 ThreadListHead : _LIST_ENTRY
+0x498 ActiveThreads : Uint4B
+0x49c ImagePathHash : Uint4B
+0x4a0 DefaultHardErrorProcessing : Uint4B
+0x4a4 LastThreadExitStatus : Int4B
+0x4a8 PrefetchTrace : _EX_FAST_REF
+0x4b0 LockedPagesList : Ptr64 Void
+0x4b8 ReadOperationCount : _LARGE_INTEGER
+0x4c0 WriteOperationCount : _LARGE_INTEGER
+0x4c8 OtherOperationCount : _LARGE_INTEGER
+0x4d0 ReadTransferCount : _LARGE_INTEGER
+0x4d8 WriteTransferCount : _LARGE_INTEGER
+0x4e0 OtherTransferCount : _LARGE_INTEGER
+0x4e8 CommitChargeLimit : Uint8B
+0x4f0 CommitCharge : Uint8B
+0x4f8 CommitChargePeak : Uint8B
+0x500 Vm : _MMSUPPORT_FULL
+0x610 MmProcessLinks : _LIST_ENTRY
+0x620 ModifiedPageCount : Uint4B
+0x624 ExitStatus : Int4B
+0x628 VadRoot : _RTL_AVL_TREE
+0x630 VadHint : Ptr64 Void
+0x638 VadCount : Uint8B
+0x640 VadPhysicalPages : Uint8B
+0x648 VadPhysicalPagesLimit : Uint8B
+0x650 AlpcContext : _ALPC_PROCESS_CONTEXT
+0x670 TimerResolutionLink : _LIST_ENTRY
+0x680 TimerResolutionStackRecord : Ptr64 _PO_DIAG_STACK_RECORD
+0x688 RequestedTimerResolution : Uint4B
+0x68c SmallestTimerResolution : Uint4B
+0x690 ExitTime : _LARGE_INTEGER
+0x698 InvertedFunctionTable : Ptr64 _INVERTED_FUNCTION_TABLE
+0x6a0 InvertedFunctionTableLock : _EX_PUSH_LOCK
+0x6a8 ActiveThreadsHighWatermark : Uint4B
+0x6ac LargePrivateVadCount : Uint4B
+0x6b0 ThreadListLock : _EX_PUSH_LOCK
+0x6b8 WnfContext : Ptr64 Void
+0x6c0 ServerSilo : Ptr64 _EJOB
+0x6c8 SignatureLevel : UChar
+0x6c9 SectionSignatureLevel : UChar
+0x6ca Protection : _PS_PROTECTION
+0x6cb HangCount : Pos 0, 3 Bits
+0x6cb GhostCount : Pos 3, 3 Bits
+0x6cb PrefilterException : Pos 6, 1 Bit
+0x6cc Flags3 : Uint4B
+0x6cc Minimal : Pos 0, 1 Bit
+0x6cc ReplacingPageRoot : Pos 1, 1 Bit
+0x6cc Crashed : Pos 2, 1 Bit
+0x6cc JobVadsAreTracked : Pos 3, 1 Bit
+0x6cc VadTrackingDisabled : Pos 4, 1 Bit
+0x6cc AuxiliaryProcess : Pos 5, 1 Bit
+0x6cc SubsystemProcess : Pos 6, 1 Bit
+0x6cc IndirectCpuSets : Pos 7, 1 Bit
+0x6cc RelinquishedCommit : Pos 8, 1 Bit
+0x6cc HighGraphicsPriority : Pos 9, 1 Bit
+0x6cc CommitFailLogged : Pos 10, 1 Bit
+0x6cc ReserveFailLogged : Pos 11, 1 Bit
+0x6cc SystemProcess : Pos 12, 1 Bit
+0x6cc HideImageBaseAddresses : Pos 13, 1 Bit
+0x6cc AddressPolicyFrozen : Pos 14, 1 Bit
+0x6cc ProcessFirstResume : Pos 15, 1 Bit
+0x6cc ForegroundExternal : Pos 16, 1 Bit
+0x6cc ForegroundSystem : Pos 17, 1 Bit
+0x6cc HighMemoryPriority : Pos 18, 1 Bit
+0x6cc EnableProcessSuspendResumeLogging : Pos 19, 1 Bit
+0x6cc EnableThreadSuspendResumeLogging : Pos 20, 1 Bit
+0x6cc SecurityDomainChanged : Pos 21, 1 Bit
+0x6cc SecurityFreezeComplete : Pos 22, 1 Bit
+0x6cc VmProcessorHost : Pos 23, 1 Bit
+0x6d0 DeviceAsid : Int4B
+0x6d8 SvmData : Ptr64 Void
+0x6e0 SvmProcessLock : _EX_PUSH_LOCK
+0x6e8 SvmLock : Uint8B
+0x6f0 SvmProcessDeviceListHead : _LIST_ENTRY
+0x700 LastFreezeInterruptTime : Uint8B
+0x708 DiskCounters : Ptr64 _PROCESS_DISK_COUNTERS
+0x710 PicoContext : Ptr64 Void
+0x718 EnclaveTable : Ptr64 Void
+0x720 EnclaveNumber : Uint8B
+0x728 EnclaveLock : _EX_PUSH_LOCK
+0x730 HighPriorityFaultsAllowed : Uint4B
+0x738 EnergyContext : Ptr64 _PO_PROCESS_ENERGY_CONTEXT
+0x740 VmContext : Ptr64 Void
+0x748 SequenceNumber : Uint8B
+0x750 CreateInterruptTime : Uint8B
+0x758 CreateUnbiasedInterruptTime : Uint8B
+0x760 TotalUnbiasedFrozenTime : Uint8B
+0x768 LastAppStateUpdateTime : Uint8B
+0x770 LastAppStateUptime : Pos 0, 61 Bits
+0x770 LastAppState : Pos 61, 3 Bits
+0x778 SharedCommitCharge : Uint8B
+0x780 SharedCommitLock : _EX_PUSH_LOCK
+0x788 SharedCommitLinks : _LIST_ENTRY
+0x798 AllowedCpuSets : Uint8B
+0x7a0 DefaultCpuSets : Uint8B
+0x798 AllowedCpuSetsIndirect : Ptr64 Uint8B
+0x7a0 DefaultCpuSetsIndirect : Ptr64 Uint8B
+0x7a8 DiskIoAttribution : Ptr64 Void
+0x7b0 DxgProcess : Ptr64 Void
+0x7b8 Win32KFilterSet : Uint4B
+0x7c0 ProcessTimerDelay : _PS_INTERLOCKED_TIMER_DELAY_VALUES
+0x7c8 KTimerSets : Uint4B
+0x7cc KTimer2Sets : Uint4B
+0x7d0 ThreadTimerSets : Uint4B
+0x7d8 VirtualTimerListLock : Uint8B
+0x7e0 VirtualTimerListHead : _LIST_ENTRY
+0x7f0 WakeChannel : _WNF_STATE_NAME
+0x7f0 WakeInfo : _PS_PROCESS_WAKE_INFORMATION
+0x820 MitigationFlags : Uint4B
+0x820 MitigationFlagsValues : <unnamed-tag>
+0x824 MitigationFlags2 : Uint4B
+0x824 MitigationFlags2Values : <unnamed-tag>
+0x828 PartitionObject : Ptr64 Void
+0x830 SecurityDomain : Uint8B
+0x838 ParentSecurityDomain : Uint8B
+0x840 CoverageSamplerContext : Ptr64 Void
+0x848 MmHotPatchContext : Ptr64 Void
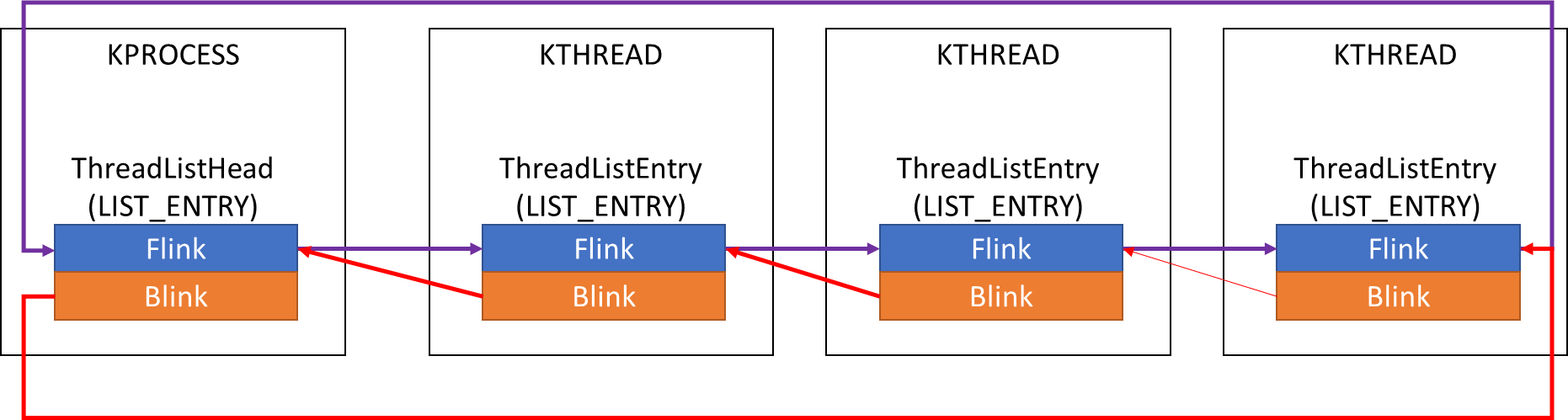
프로세스에 속해 있는 여러 쓰레드는 EPROCESS 구조체에 있는 ThreadListHead를 이용해서 Doubly Linked List로 관리

3. KPROCESS 구조체
KPROCESS 구조체는 Scheduling 목적으로 사용됩니다.
2: kd> dt nt!_KPROCESS ffffbc0c19c33080
+0x000 Header : _DISPATCHER_HEADER
+0x018 ProfileListHead : _LIST_ENTRY [ 0xffffbc0c`19c33098 - 0xffffbc0c`19c33098 ]
+0x028 DirectoryTableBase : 0x00000001`161d5000
+0x030 ThreadListHead : _LIST_ENTRY [ 0xffffbc0c`1a1a5378 - 0xffffbc0c`1a19c378 ]
+0x040 ProcessLock : 0
+0x044 ProcessTimerDelay : 0
+0x048 DeepFreezeStartTime : 0
+0x050 Affinity : _KAFFINITY_EX
+0x0f8 ReadyListHead : _LIST_ENTRY [ 0xffffbc0c`19c33178 - 0xffffbc0c`19c33178 ]
+0x108 SwapListEntry : _SINGLE_LIST_ENTRY
+0x110 ActiveProcessors : _KAFFINITY_EX
+0x1b8 AutoAlignment : 0y0
+0x1b8 DisableBoost : 0y0
+0x1b8 DisableQuantum : 0y0
+0x1b8 DeepFreeze : 0y0
+0x1b8 TimerVirtualization : 0y0
+0x1b8 CheckStackExtents : 0y1
+0x1b8 CacheIsolationEnabled : 0y0
+0x1b8 PpmPolicy : 0y101
+0x1b8 ActiveGroupsMask : 0y00000000000000000001 (0x1)
+0x1b8 VaSpaceDeleted : 0y0
+0x1b8 ReservedFlags : 0y0
+0x1b8 ProcessFlags : 0n1696
+0x1bc BasePriority : 8 ''
+0x1bd QuantumReset : 36 '$'
+0x1be Visited : 0 ''
+0x1bf Flags : _KEXECUTE_OPTIONS
+0x1c0 ThreadSeed : [20] 2
+0x210 IdealNode : [20] 0
+0x238 IdealGlobalNode : 0
+0x23a Spare1 : 0
+0x23c StackCount : _KSTACK_COUNT
+0x240 ProcessListEntry : _LIST_ENTRY [ 0xffffbc0c`1a1b12c0 - 0xffffbc0c`1a1ab300 ]
+0x250 CycleTime : 0x113d294
+0x258 ContextSwitches : 0x8c
+0x260 SchedulingGroup : (null)
+0x268 FreezeCount : 0
+0x26c KernelTime : 1
+0x270 UserTime : 1
+0x274 ReadyTime : 0
+0x278 UserDirectoryTableBase : 0
+0x280 AddressPolicy : 0 ''
+0x281 Spare2 : [71] ""
+0x2c8 InstrumentationCallback : (null)
+0x2d0 SecureState : <unnamed-tag>
KPROCESS 구조체도 EPROCESS와 마찬가지로 모든 쓰레드와 Doubly Linked List로 연결
4. PEB(Process Environment Block)
PEB는 EPROCESS 구조체에 포인터가 있지만, User mode를 위한 구조체입니다.
PEB에는 프로세스에 로드된 모든 모듈 정보를 포함하며, 프로세스가 실행할 때 사용하는 환경 변수(Path 등)도 PEB를 통해 조회 가능합니다.
특정 프로세스의 PEB를 조회하기 위해서는 해당 프로세스로 Context Switch를 해야 올바르게 조회 가능합니다.
Windbg에서 프로세스로 Context Switch는 .process 명령어 이용할 수 있습니다.
| 3: kd> .process /i /p /r ffffbc0c19c33080 You need to continue execution (press 'g' <enter>) for the context to be switched. When the debugger breaks in again, you will be in the new process context. 3: kd> g Break instruction exception - code 80000003 (first chance) nt!DbgBreakPointWithStatus: fffff806`3ee73600 cc int 3 |
!peb extension을 이용하면 현재 Context 의 EPROCESS 구조체에 있는 Peb 값을 이용하여 PEB 정보를 표시
3: kd> !peb
PEB at 000000c1e88f0000
InheritedAddressSpace: No
ReadImageFileExecOptions: No
BeingDebugged: No
ImageBaseAddress: 00007ff74f230000
NtGlobalFlag: 0
NtGlobalFlag2: 0
Ldr 00007ffd8a9e53a0
Ldr.Initialized: Yes
Ldr.InInitializationOrderModuleList: 0000029440db23f0 . 000002945fdde4d0
Ldr.InLoadOrderModuleList: 0000029440db2560 . 000002945fdde4b0
Ldr.InMemoryOrderModuleList: 0000029440db2570 . 000002945fdde4c0
Base TimeStamp Module
29440b80000 c452e206 May 17 16:02:30 2074 C:\Windows\system32\ServerManager.exe
7ffd8a880000 1f1a0210 Jul 15 16:56:00 1986 C:\Windows\SYSTEM32\ntdll.dll
7ffd75f00000 3fc02147 Nov 23 11:53:59 2003 C:\Windows\SYSTEM32\MSCOREE.DLL
7ffd89ad0000 250a0626 Sep 10 15:58:46 1989 C:\Windows\System32\KERNEL32.dll
7ffd872f0000 fb6790ac Aug 30 07:07:40 2103 C:\Windows\System32\KERNELBASE.dll
7ffd895f0000 b12069f9 Mar 02 22:51:53 2064 C:\Windows\System32\ADVAPI32.dll
7ffd89b90000 f362c2f9 May 25 04:58:49 2099 C:\Windows\System32\msvcrt.dll
7ffd8a290000 7d59184a Aug 22 13:08:42 2036 C:\Windows\System32\sechost.dll
7ffd8a510000 755dd37f May 25 16:34:23 2032 C:\Windows\System32\RPCRT4.dll
7ffd75e60000 5d490c3e Aug 06 14:12:30 2019 C:\Windows\Microsoft.NET\Framework64\v4.0.30319\mscoreei.dll
7ffd88010000 4392c932 Dec 04 19:47:14 2005 C:\Windows\System32\SHLWAPI.dll
7ffd896a0000 c366780e Nov 19 08:15:26 2073 C:\Windows\System32\combase.dll
7ffd87140000 15f8b9b3 Sep 06 20:00:03 1981 C:\Windows\System32\ucrtbase.dll
7ffd87590000 94fbdec9 Mar 17 04:08:57 2049 C:\Windows\System32\bcryptPrimitives.dll
7ffd8a330000 f945b633 Jul 12 06:10:11 2102 C:\Windows\System32\GDI32.dll
7ffd877f0000 1eac2959 Apr 23 09:14:17 1986 C:\Windows\System32\gdi32full.dll
7ffd87990000 448f33c2 Jun 14 06:53:06 2006 C:\Windows\System32\msvcp_win.dll
7ffd8a0b0000 38186bc1 Oct 29 00:29:05 1999 C:\Windows\System32\USER32.dll
7ffd87a30000 ff141dbb Aug 12 17:20:11 2105 C:\Windows\System32\win32u.dll
7ffd899d0000 789dcfe1 Feb 15 18:24:49 2034 C:\Windows\System32\IMM32.DLL
7ffd868d0000 be88784d Apr 19 05:32:13 2071 C:\Windows\System32\kernel.appcore.dll
7ffd7c8b0000 b11b88e5 Feb 28 06:02:29 2064 C:\Windows\system32\VERSION.dll
7ffd69220000 5d490db7 Aug 06 14:18:47 2019 C:\Windows\Microsoft.NET\Framework64\v4.0.30319\clr.dll
7ffd741a0000 5849f946 Dec 09 09:22:30 2016 C:\Windows\SYSTEM32\MSVCR120_CLR0400.dll
7ffd67c80000 5d490c48 Aug 06 14:12:40 2019 C:\Windows\assembly\NativeImages_v4.0.30319_64\mscorlib\5748a97e77ef4e55dc65fc7d20d480e3\mscorlib.ni.dll
7ffd8a6f0000 197cc46a Jul 21 12:45:46 1983 C:\Windows\System32\ole32.dll
7ffd84e50000 607fb06a Apr 21 13:56:10 2021 C:\Windows\system32\uxtheme.dll
7ffd87a80000 fe800ac7 Apr 22 09:43:51 2105 C:\Windows\System32\CRYPTSP.dll
7ffd85c00000 eb037b86 Dec 11 11:46:30 2094 C:\Windows\system32\rsaenh.dll
7ffd87a50000 4d019572 Dec 10 11:50:26 2010 C:\Windows\System32\bcrypt.dll
7ffd86250000 210d2d73 Jul 29 08:02:11 1987 C:\Windows\system32\CRYPTBASE.dll
7ffd67030000 5d37b695 Jul 24 10:38:29 2019 C:\Windows\assembly\NativeImages_v4.0.30319_64\System\12f61e3a15a903def0bce11cfcee51bc\System.ni.dll
7ffd665e0000 5de6d7d8 Dec 04 06:47:04 2019 C:\Windows\assembly\NativeImages_v4.0.30319_64\System.Core\b39a619d52b544806411ac8c402bfe68\System.Core.ni.dll
7ffd660e0000 5de6df3b Dec 04 07:18:35 2019 C:\Windows\assembly\NativeImages_v4.0.30319_64\WindowsBase\619671aa4b77402eaa287ef86ffc8fc2\WindowsBase.ni.dll
7ffd65300000 5de6e202 Dec 04 07:30:26 2019 C:\Windows\assembly\NativeImages_v4.0.30319_64\PresentationCore\caf51f6e6e369e4bcf5e76a67ae317bf\PresentationCore.ni.dll
7ffd63ca0000 5de6df43 Dec 04 07:18:43 2019 C:\Windows\assembly\NativeImages_v4.0.30319_64\Presentatio5ae0f00f#\fd146bf8e59d0ef2151f5f0834676836\PresentationFramework.ni.dll
7ffd639e0000 5de6df39 Dec 04 07:18:33 2019 C:\Windows\assembly\NativeImages_v4.0.30319_64\System.Xaml\e555d8e06d1d188ba1d4b19a38da6a99\System.Xaml.ni.dll
7ffd78c40000 ab4cb5dd Jan 26 11:13:49 2061 C:\Windows\SYSTEM32\dwrite.dll
7ffd63830000 5de6e22a Dec 04 07:31:06 2019 C:\Windows\Microsoft.NET\Framework64\v4.0.30319\WPF\wpfgfx_v0400.dll
7ffd87cf0000 de08ca6c Jan 17 04:01:00 2088 C:\Windows\System32\OLEAUT32.dll
7ffd63780000 5849f94a Dec 09 09:22:34 2016 C:\Windows\system32\MSVCP120_CLR0400.dll
7ffd63670000 5de6e211 Dec 04 07:30:41 2019 C:\Windows\Microsoft.NET\Framework64\v4.0.30319\WPF\PresentationNative_v0400.dll
7ffd63540000 5d490c60 Aug 06 14:13:04 2019 C:\Windows\Microsoft.NET\Framework64\v4.0.30319\clrjit.dll
7ffd62ef0000 ba484dfc Jan 13 20:05:32 2069 C:\Windows\assembly\NativeImages_v4.0.30319_64\Microsoft.Wf493a5fb#\f6ed928133eab13cfd78e4812d0b7e84\Microsoft.Windows.ServerManager.Common.ni.dll
7ffd81ce0000 352f1e7b Apr 11 16:40:43 1998 C:\Windows\SYSTEM32\WindowsCodecs.dll
7ffd87b80000 3243efc5 Sep 21 22:38:13 1996 C:\Windows\System32\MSCTF.dll
7ffd62dc0000 5c09ba33 Dec 07 09:09:23 2018 C:\Windows\assembly\NativeImages_v4.0.30319_64\System.Configuration\7f8ac0b51d8f00e538b5e6801aa22253\System.Configuration.ni.dll
7ffd62530000 5b6947d7 Aug 07 16:18:47 2018 C:\Windows\assembly\NativeImages_v4.0.30319_64\System.Xml\f58bcb1d98c88dc2c1fcdf12c329fe47\System.Xml.ni.dll
7ffd880f0000 8126cd3a Aug 31 02:56:10 2038 C:\Windows\System32\shell32.dll
7ffd87240000 ca7e64ca Aug 27 18:09:30 2077 C:\Windows\System32\cfgmgr32.dll
7ffd8a640000 9a0e77eb Nov 27 04:24:27 2051 C:\Windows\System32\shcore.dll
7ffd869f0000 9a536081 Jan 18 10:50:57 2052 C:\Windows\System32\windows.storage.dll
7ffd86910000 36191177 Oct 06 03:35:35 1998 C:\Windows\System32\profapi.dll
7ffd86870000 8941f3e3 Dec 22 03:54:27 2042 C:\Windows\System32\powrprof.dll
7ffd85180000 674bb59c Dec 01 10:02:20 2024 C:\Windows\system32\dwmapi.dll
7ffd87610000 5546f275 May 04 13:15:49 2015 C:\Windows\System32\CRYPT32.dll
7ffd868f0000 ac91a4b2 Sep 29 22:27:14 2061 C:\Windows\System32\MSASN1.dll
7ffd7e380000 6be78ecd May 15 08:31:25 2027 C:\Windows\system32\urlmon.dll
7ffd803c0000 80235707 Feb 15 07:34:47 2038 C:\Windows\system32\iertutil.dll
7ffd86770000 ebd3b7f6 May 18 10:35:50 2095 C:\Windows\system32\SspiCli.dll
7ffd827c0000 296f9bb4 Jan 12 10:36:52 1992 C:\Windows\system32\PROPSYS.dll
7ffd62490000 5b694f15 Aug 07 16:49:41 2018 C:\Windows\assembly\NativeImages_v4.0.30319_64\Presentatioaec034ca#\6486e0eb5693bb4b3d5d451a676315d0\PresentationFramework.Aero2.ni.dll
7ffd87f50000 aaba4fa9 Oct 07 10:06:49 2060 C:\Windows\System32\clbcatq.dll
7ffd622f0000 fc1b9e5e Jan 13 20:54:06 2104 C:\Windows\system32\d3d9.dll
7ffd7fa60000 6cee4cbf Nov 30 15:35:43 2027 C:\Windows\system32\d3d10warp.dll
7ffd84c60000 645d63a8 May 12 06:52:40 2023 C:\Windows\SYSTEM32\wtsapi32.dll
7ffd86710000 d1e21847 Aug 01 15:31:35 2081 C:\Windows\SYSTEM32\WINSTA.dll
7ffd77dc0000 28590552 Jun 15 03:05:06 1991 C:\Windows\system32\dataexchange.dll
7ffd83aa0000 13a31007 Jun 10 11:52:55 1980 C:\Windows\system32\d3d11.dll
7ffd84330000 517b0b92 Apr 27 08:19:46 2013 C:\Windows\system32\dcomp.dll
7ffd85540000 8bbb106a Apr 15 09:20:58 2044 C:\Windows\system32\dxgi.dll
7ffd84f20000 0d83a788 Mar 09 14:05:12 1977 C:\Windows\system32\twinapi.appcore.dll
7ffd85130000 fd3b8fed Aug 19 06:45:17 2104 C:\Windows\system32\RMCLIENT.dll
7ffd75390000 74f763f7 Mar 08 23:47:19 2032 C:\Windows\system32\msctfui.dll
7ffd6d1a0000 61476b0c Sep 20 01:53:32 2021 C:\Windows\SYSTEM32\UIAutomationCore.dll
7ffd81520000 36cd57fa Feb 19 21:24:26 1999 C:\Windows\SYSTEM32\Bcp47Langs.dll
7ffd62100000 5b6947cc Aug 07 16:18:36 2018 C:\Windows\assembly\NativeImages_v4.0.30319_64\System.Drawing\1883282d05b2edc8c7a85d6253709126\System.Drawing.ni.dll
7ffd611b0000 5c09ba04 Dec 07 09:08:36 2018 C:\Windows\assembly\NativeImages_v4.0.30319_64\System.Windows.Forms\4bc868557e259ea96dea29fd3317884d\System.Windows.Forms.ni.dll
7ffd83600000 3119962f Feb 08 15:20:31 1996 C:\Windows\system32\D3DCOMPILER_47.dll
7ffd6fd60000 700dafec Jul 28 23:59:56 2029 C:\Windows\system32\mscms.dll
7ffd82ce0000 b5672678 Jun 11 07:55:52 2066 C:\Windows\system32\ColorAdapterClient.dll
7ffd867a0000 153decdb Apr 18 03:24:27 1981 C:\Windows\system32\USERENV.dll
7ffd610f0000 bae4dc8c May 12 14:07:24 2069 C:\Windows\system32\WindowsCodecsExt.dll
7ffd84980000 01dd0441 Dec 29 04:49:21 1970 C:\Windows\system32\WINMM.dll
7ffd84860000 61c36296 Dec 23 02:38:30 2021 C:\Windows\system32\WINMMBASE.dll
7ffd78260000 a60abe19 Apr 11 12:38:01 2058 C:\Windows\system32\Microsoft.Management.Infrastructure.Native.Unmanaged.DLL
7ffd7ac00000 eed387eb Dec 20 20:11:39 2096 C:\Windows\system32\mi.dll
7ffd7ae50000 21016feb Jul 20 10:18:35 1987 C:\Windows\system32\miutils.dll
7ffd79e60000 0fb50d5f May 09 10:01:19 1978 C:\Windows\system32\wmidcom.dll
7ffd85c40000 8735b5a3 Nov 19 12:21:07 2041 C:\Windows\system32\DPAPI.DLL
7ffd79ad0000 80ed95b9 Jul 18 17:20:09 2038 C:\Windows\system32\wbem\wbemprox.dll
7ffd89a00000 19b2d7cc Aug 31 13:10:52 1983 C:\Windows\System32\WS2_32.dll
7ffd7aec0000 264de62a May 14 07:56:42 1990 C:\Windows\SYSTEM32\wbemcomn.dll
7ffd799e0000 42167f4e Feb 19 08:50:38 2005 C:\Windows\system32\wbem\wbemsvc.dll
7ffd79300000 c27bfeee May 25 11:48:14 2073 C:\Windows\system32\wbem\fastprox.dll
7ffd86080000 9cffe601 Jun 20 16:10:57 2053 C:\Windows\system32\mswsock.dll
7ffd5e680000 df2416c1 Aug 19 01:18:09 2088 C:\Windows\assembly\NativeImages_v4.0.30319_64\Microsoft.W9e7db7c5#\816b8d0e53517ec40d0cfbc2b67f9004\Microsoft.Windows.FileServer.Management.Plugin.UI.ni.dll
7ffd5e170000 da6a47ae Feb 13 09:24:14 2086 C:\Windows\assembly\NativeImages_v4.0.30319_64\Microsoft.W7b7c0837#\7196412e901a030915ef75743a1237ca\Microsoft.Windows.FileServer.Management.Plugin.ni.dll
SubSystemData: 00007ffd85104440
ProcessHeap: 00000293be8a0000
ProcessParameters: 00000293be8a1c10
CurrentDirectory: 'C:\Users\Administrator\'
WindowTitle: 'C:\Windows\system32\notepad.exe'
ImageFile: 'C:\Windows\system32\notepad.exe'
CommandLine: '"C:\Windows\system32\notepad.exe" '
DllPath: '< Name not readable >'
Environment: 00000293be8a0fe0
=::=::\
ALLUSERSPROFILE=C:\ProgramData
APPDATA=C:\Users\Administrator\AppData\Roaming
CommonProgramFiles=C:\Program Files\Common Files
CommonProgramFiles(x86)=C:\Program Files (x86)\Common Files
CommonProgramW6432=C:\Program Files\Common Files
COMPUTERNAME=WIN-5MMJK462VCF
ComSpec=C:\Windows\system32\cmd.exe
DriverData=C:\Windows\System32\Drivers\DriverData
FPS_BROWSER_APP_PROFILE_STRING=Internet Explorer
FPS_BROWSER_USER_PROFILE_STRING=Default
HOMEDRIVE=C:
HOMEPATH=\Users\Administrator
LOCALAPPDATA=C:\Users\Administrator\AppData\Local
LOGONSERVER=\\WIN-5MMJK462VCF
NUMBER_OF_PROCESSORS=8
OS=Windows_NT
Path=C:\Windows\system32;C:\Windows;C:\Windows\System32\Wbem;C:\Windows\System32\WindowsPowerShell\v1.0\;C:\Windows\System32\OpenSSH\;C:\Users\Administrator\AppData\Local\Microsoft\WindowsApps;
PATHEXT=.COM;.EXE;.BAT;.CMD;.VBS;.VBE;.JS;.JSE;.WSF;.WSH;.MSC
PROCESSOR_ARCHITECTURE=AMD64
PROCESSOR_IDENTIFIER=Intel64 Family 6 Model 85 Stepping 7, GenuineIntel
PROCESSOR_LEVEL=6
PROCESSOR_REVISION=5507
ProgramData=C:\ProgramData
ProgramFiles=C:\Program Files
ProgramFiles(x86)=C:\Program Files (x86)
ProgramW6432=C:\Program Files
PSModulePath=C:\Program Files\WindowsPowerShell\Modules;C:\Windows\system32\WindowsPowerShell\v1.0\Modules
PUBLIC=C:\Users\Public
SESSIONNAME=Console
SystemDrive=C:
SystemRoot=C:\Windows
TEMP=C:\Users\ADMINI~1\AppData\Local\Temp
TMP=C:\Users\ADMINI~1\AppData\Local\Temp
USERDOMAIN=WIN-5MMJK462VCF
USERDOMAIN_ROAMINGPROFILE=WIN-5MMJK462VCF
USERNAME=Administrator
USERPROFILE=C:\Users\Administrator
windir=C:\Windows
PEB 정보에는 우리가 흔히 볼 수 있는 정보 중 CommandLine 정보도 확인 가능
| 3: kd> !peb PEB at 000000c1e88f0000 ... WindowTitle: 'C:\Windows\system32\notepad.exe' ImageFile: 'C:\Windows\system32\notepad.exe' CommandLine: '"C:\Windows\system32\notepad.exe" ' DllPath: '< Name not readable >' Environment: 00000293be8a0fe0 =::=::\ ALLUSERSPROFILE=C:\ProgramData ... |
PEB 구조체의 주소를 이용하여 직접 조회도 가능
2: kd> !process ffffbc0c19c33080 0
PROCESS ffffbc0c19c33080
SessionId: 1 Cid: 0318 Peb: c1e88f0000 ParentCid: 1010
DirBase: 1161d5000 ObjectTable: ffff918d8b13f600 HandleCount: 245.
Image: notepad.exe
2: kd> dt _PEB c1e88f0000
ntdll!_PEB
+0x000 InheritedAddressSpace : 0 ''
+0x001 ReadImageFileExecOptions : 0 ''
+0x002 BeingDebugged : 0 ''
+0x003 BitField : 0x4 ''
+0x003 ImageUsesLargePages : 0y0
+0x003 IsProtectedProcess : 0y0
+0x003 IsImageDynamicallyRelocated : 0y1
+0x003 SkipPatchingUser32Forwarders : 0y0
+0x003 IsPackagedProcess : 0y0
+0x003 IsAppContainer : 0y0
+0x003 IsProtectedProcessLight : 0y0
+0x003 IsLongPathAwareProcess : 0y0
+0x004 Padding0 : [4] ""
+0x008 Mutant : 0xffffffff`ffffffff Void
+0x010 ImageBaseAddress : 0x00007ff7`4f230000 Void
+0x018 Ldr : 0x00007ffd`8a9e53a0 _PEB_LDR_DATA
+0x020 ProcessParameters : 0x00000293`be8a1c10 _RTL_USER_PROCESS_PARAMETERS
+0x028 SubSystemData : 0x00007ffd`85104440 Void
+0x030 ProcessHeap : 0x00000293`be8a0000 Void
+0x038 FastPebLock : 0x00007ffd`8a9e4fa0 _RTL_CRITICAL_SECTION
+0x040 AtlThunkSListPtr : (null)
+0x048 IFEOKey : (null)
+0x050 CrossProcessFlags : 0
+0x050 ProcessInJob : 0y0
+0x050 ProcessInitializing : 0y0
+0x050 ProcessUsingVEH : 0y0
+0x050 ProcessUsingVCH : 0y0
+0x050 ProcessUsingFTH : 0y0
+0x050 ProcessPreviouslyThrottled : 0y0
+0x050 ProcessCurrentlyThrottled : 0y0
+0x050 ProcessImagesHotPatched : 0y0
+0x050 ReservedBits0 : 0y000000000000000000000000 (0)
+0x054 Padding1 : [4] ""
+0x058 KernelCallbackTable : 0x00007ffd`8a138000 Void
+0x058 UserSharedInfoPtr : 0x00007ffd`8a138000 Void
+0x060 SystemReserved : 0
+0x064 AtlThunkSListPtr32 : 0
+0x068 ApiSetMap : 0x00000293`be840000 Void
+0x070 TlsExpansionCounter : 0
+0x074 Padding2 : [4] ""
+0x078 TlsBitmap : 0x00007ffd`8a9e5300 Void
+0x080 TlsBitmapBits : [2] 0xffffffff
+0x088 ReadOnlySharedMemoryBase : 0x00007df4`b9c60000 Void
+0x090 SharedData : (null)
+0x098 ReadOnlyStaticServerData : 0x00007df4`b9c60750 -> (null)
+0x0a0 AnsiCodePageData : 0x00007df5`bbda0000 Void
+0x0a8 OemCodePageData : 0x00007df5`bbdb0228 Void
+0x0b0 UnicodeCaseTableData : 0x00007df5`bbdc0650 Void
+0x0b8 NumberOfProcessors : 8
+0x0bc NtGlobalFlag : 0
+0x0c0 CriticalSectionTimeout : _LARGE_INTEGER 0xffffe86d`079b8000
+0x0c8 HeapSegmentReserve : 0x100000
+0x0d0 HeapSegmentCommit : 0x2000
+0x0d8 HeapDeCommitTotalFreeThreshold : 0x10000
+0x0e0 HeapDeCommitFreeBlockThreshold : 0x1000
+0x0e8 NumberOfHeaps : 4
+0x0ec MaximumNumberOfHeaps : 0x10
+0x0f0 ProcessHeaps : 0x00007ffd`8a9e3b80 -> 0x00000293`be8a0000 Void
+0x0f8 GdiSharedHandleTable : 0x00000293`bed20000 Void
+0x100 ProcessStarterHelper : (null)
+0x108 GdiDCAttributeList : 0x14
+0x10c Padding3 : [4] ""
+0x110 LoaderLock : 0x00007ffd`8a9df4f8 _RTL_CRITICAL_SECTION
+0x118 OSMajorVersion : 0xa
+0x11c OSMinorVersion : 0
+0x120 OSBuildNumber : 0x4563
+0x122 OSCSDVersion : 0
+0x124 OSPlatformId : 2
+0x128 ImageSubsystem : 2
+0x12c ImageSubsystemMajorVersion : 0xa
+0x130 ImageSubsystemMinorVersion : 0
+0x134 Padding4 : [4] ""
+0x138 ActiveProcessAffinityMask : 0xff
+0x140 GdiHandleBuffer : [60] 0
+0x230 PostProcessInitRoutine : (null)
+0x238 TlsExpansionBitmap : 0x00007ffd`8a9e52e0 Void
+0x240 TlsExpansionBitmapBits : [32] 1
+0x2c0 SessionId : 1
+0x2c4 Padding5 : [4] ""
+0x2c8 AppCompatFlags : _ULARGE_INTEGER 0x0
+0x2d0 AppCompatFlagsUser : _ULARGE_INTEGER 0x0
+0x2d8 pShimData : 0x00000293`be880000 Void
+0x2e0 AppCompatInfo : (null)
+0x2e8 CSDVersion : _UNICODE_STRING ""
+0x2f8 ActivationContextData : 0x00000293`be870000 _ACTIVATION_CONTEXT_DATA
+0x300 ProcessAssemblyStorageMap : 0x00000293`be8ab4b0 _ASSEMBLY_STORAGE_MAP
+0x308 SystemDefaultActivationContextData : 0x00000293`be860000 _ACTIVATION_CONTEXT_DATA
+0x310 SystemAssemblyStorageMap : (null)
+0x318 MinimumStackCommit : 0
+0x320 FlsCallback : 0x00000293`be8b7420 _FLS_CALLBACK_INFO
+0x328 FlsListHead : _LIST_ENTRY [ 0x00000293`be8b6b20 - 0x00000293`be8f9b50 ]
+0x338 FlsBitmap : 0x00007ffd`8a9e5360 Void
+0x340 FlsBitmapBits : [4] 0x7f
+0x350 FlsHighIndex : 6
+0x358 WerRegistrationData : (null)
+0x360 WerShipAssertPtr : (null)
+0x368 pUnused : (null)
+0x370 pImageHeaderHash : (null)
+0x378 TracingFlags : 0
+0x378 HeapTracingEnabled : 0y0
+0x378 CritSecTracingEnabled : 0y0
+0x378 LibLoaderTracingEnabled : 0y0
+0x378 SpareTracingBits : 0y00000000000000000000000000000 (0)
+0x37c Padding6 : [4] ""
+0x380 CsrServerReadOnlySharedMemoryBase : 0x00007df4`d67c0000
+0x388 TppWorkerpListLock : 0
+0x390 TppWorkerpList : _LIST_ENTRY [ 0x000000c1`e8bffc10 - 0x000000c1`e8c7f640 ]
+0x3a0 WaitOnAddressHashTable : [128] (null)
+0x7a0 TelemetryCoverageHeader : (null)
+0x7a8 CloudFileFlags : 0
+0x7ac CloudFileDiagFlags : 0
+0x7b0 PlaceholderCompatibilityMode : 0 ''
+0x7b1 PlaceholderCompatibilityModeReserved : [7] ""
+0x7b8 LeapSecondData : 0x00007df5`bbd90000 _LEAP_SECOND_DATA
+0x7c0 LeapSecondFlags : 0
+0x7c0 SixtySecondEnabled : 0y0
+0x7c0 Reserved : 0y0000000000000000000000000000000 (0)
+0x7c4 NtGlobalFlag2 : 0
'Debugging > Windows' 카테고리의 다른 글
| Objects and Handles (2) | 2023.04.15 |
|---|---|
| 프로세스(EPROCESS, KPROCESS, PEB, HANDLE...) - (2) (0) | 2023.02.05 |
| How to configure network debugging using windbg (0) | 2023.01.25 |
| How to collect performance log using performance monitor (0) | 2022.11.03 |
| Pending되어 있는 NBL 중 Network Monitor를 통한 Packet 확인 (0) | 2022.08.30 |


