Security
Security Reference Monitor(SRM)
- SRM은 Security Access Check, Privilege Check, Auditing Events를 구현하는 Kernel-Mode Routine
Local Security Authority subsystem(LSASS)
- 대부분의 Security Operation 담당 User-Mode Process
- LSASS policy database는 아래 관련 정보 보관
- Logon 정보
- Cached Logon 정보
- 권한 및 감사 정보
- Domain Trust 정보
- 대부분의 LSA Policy 함수는 Policy Object에 대한 Handle이 필요
- 이를 위해 LsaOpenPolicy 함수 사용
https://learn.microsoft.com/en-us/windows/win32/secmgmt/opening-a-policy-object-handle
| #include <windows.h> #define TARGET_SYSTEM_NAME L"mysystem" LSA_HANDLE GetPolicyHandle() { LSA_OBJECT_ATTRIBUTES ObjectAttributes; WCHAR SystemName[] = TARGET_SYSTEM_NAME; USHORT SystemNameLength; LSA_UNICODE_STRING lusSystemName; NTSTATUS ntsResult; LSA_HANDLE lsahPolicyHandle; // Object attributes are reserved, so initialize to zeros. ZeroMemory(&ObjectAttributes, sizeof(ObjectAttributes)); //Initialize an LSA_UNICODE_STRING to the server name. SystemNameLength = wcslen(SystemName); lusSystemName.Buffer = SystemName; lusSystemName.Length = SystemNameLength * sizeof(WCHAR); lusSystemName.MaximumLength = (SystemNameLength+1) * sizeof(WCHAR); // Get a handle to the Policy object. ntsResult = LsaOpenPolicy( &lusSystemName, //Name of the target system. &ObjectAttributes, //Object attributes. POLICY_ALL_ACCESS, //Desired access permissions. &lsahPolicyHandle //Receives the policy handle. ); if (ntsResult != STATUS_SUCCESS) { // An error occurred. Display it as a win32 error code. wprintf(L"OpenPolicy returned %lu\n", LsaNtStatusToWinError(ntsResult)); return NULL; } return lsahPolicyHandle; } |
- 주로 사용되는 LSA Policy 함수 : Application이 SID로 이름을 찾거나, 이름으로 SID를 찾을 때 사용
- LsaLookupSids function (ntsecapi.h) : https://learn.microsoft.com/en-us/windows/win32/api/ntsecapi/nf-ntsecapi-lsalookupsids
- LsaLookupNames function (ntsecapi.h) : https://learn.microsoft.com/en-us/windows/win32/api/ntsecapi/nf-ntsecapi-lsalookupnames
- 이 함수들은 LSASS.exe 프로세스 내에서 LSA 관련 Thread가 처리
- LSA는 이미 가지고 있던 정보를 이용하여 SID를 확인해주거나, 할 수 없는 경우 Domain Controller에게 해당 정보를 전송 ## 기존 Mapping 결과가 LSA in-memory cache에 보관
- 이 정보는 Windows Server(Client)와 Domain Controller 간 Netlogon Secure Channel을 통해 전송
| ## The LsaLookupSids function looks up the names that correspond to an array of security identifiers (SIDs). NTSTATUS LsaLookupSids( [in] LSA_HANDLE PolicyHandle, [in] ULONG Count, [in] PSID *Sids, [out] PLSA_REFERENCED_DOMAIN_LIST *ReferencedDomains, [out] PLSA_TRANSLATED_NAME *Names ); ## The LsaLookupNames function retrieves the security identifiers (SIDs) that correspond to an array of user, group, or local group names. NTSTATUS LsaLookupNames( [in] LSA_HANDLE PolicyHandle, [in] ULONG Count, [in] PLSA_UNICODE_STRING Names, [out] PLSA_REFERENCED_DOMAIN_LIST *ReferencedDomains, [out] PLSA_TRANSLATED_SID *Sids ); |
Security Account Manager(SAM)
- LSASS 프로세스 Context 하에서 실행되는 서비스로 local SAM database를 관리
- SAM에는 local(Domain Controller가 아닌)에서 생성한 User와 Group 정보를 포함
Active Directory
- User, Group, Computer, User Rights와 Domain 및 Forest 기반 정보를 담고 있는 Database
- 이 정보는 Domain 내에 각 Domain Controller에 있는 local AD database에 저장
- AD Database 관련 기능은 LSASS.exe 프로세스에 로드되는 Library에 의해 제공
- AD 관련 API
- AD Replication
- Trigger, Perform, Translate, Add, Gather, Get 등 제공
- LDAP
- LDAP은 TCP/IP Stack 위에서 실행되는 Directory Service Protocol
- Connect, Search, Modify 등 제공
- AD Replication
Authentication Packages
- Authentication Package들은 LSASS 프로세스에 로드되는 Library로 이 Library들은 Security Support Provider Interface(SSPI)의 Subcomponent
- 이 Subcomponent들은 각각 Kerberos, NTLM, Digest, CredSSP와 SSL을 구현
- 한 가지 negotiation package는 직접적인 인증 관련 Library가 아니라, SSPI Client가 인증 Package를 직접 선택하지 않아도 인증받을 수 있도록 해주는 역할
- negotiation package의 경우 우선, Kerberos 인증을 시도하고 실패하면 NTLM으로 fall back 처리
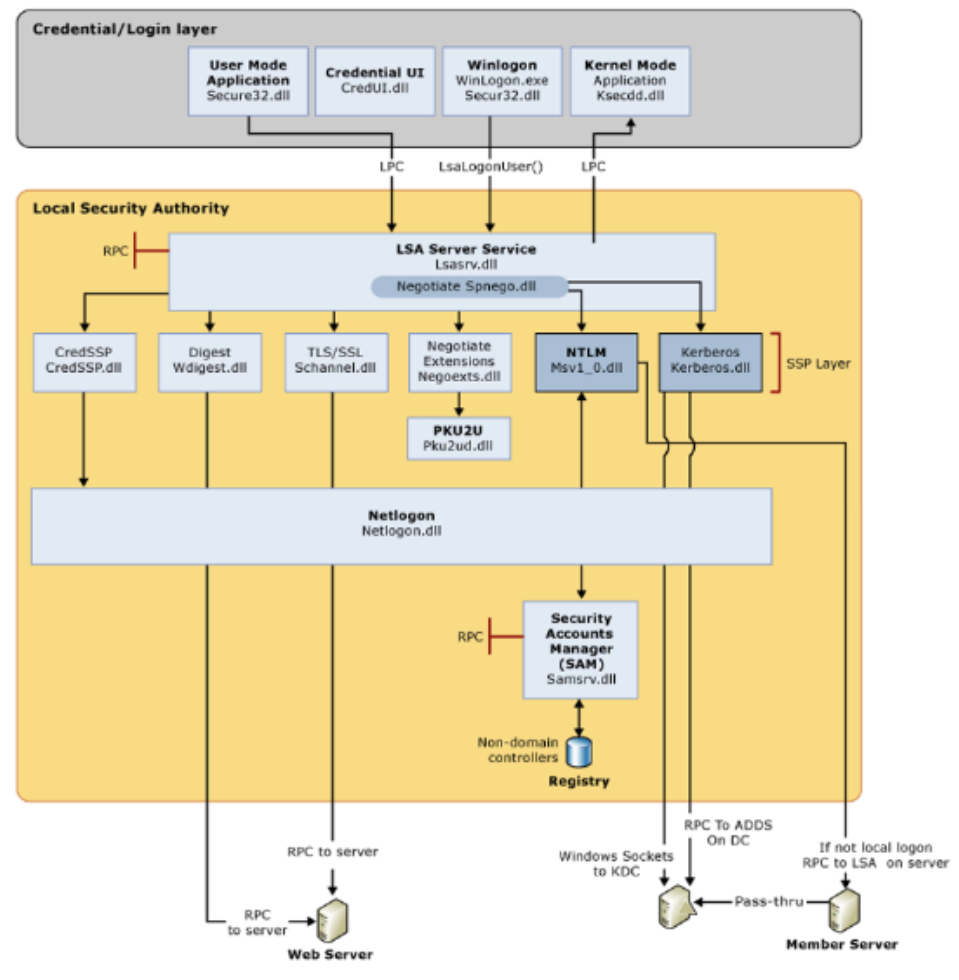
- Security Support Provider Interface(SSPI)
- SSPI는 Windows에서 지원하는 여러 Security Support Provider(SSP)를 위한 공통 인터페이스를 제공
- 따라서, 개발자들은 인증 프로토콜을 완벽히 이해할 필요없이, SSPI가 제공하는 인터페이스를 통해서 Client/Server 보안 구현 가능
- Kerberos
- Kerberos는 인증 토큰과 Symmetric Session Key의 생성 및 배포를 위해 Key Distribution Center(KDC)라는 Trusted 3rd Party를 이용
- Client는 인증 Ticket을 요청하고, 이 요청을 받은 KDC는 Ticket을 생성하여 Client에게 전달
- Client는 전달받은 Ticket을 이용하여, 접근하고자 하는 자원(서버, 파일 공유 등)에 접근
- https://learn.microsoft.com/en-us/openspecs/windows_protocols/ms-kile/b4af186e-b2ff-43f9-b18e-eedb366abf13
- NTLM
- Challenge/Response Mechanism 이용
- Client NTLM을 이용하여 접근을 시도하면, Server는 Random Number인 Challenge를 생성하여 Client에게 전송
- Client는 이 Challenge를 사용자 Password의 Hash를 이용하여 Challenge 값을 Encrypt하여 Server로 전송, 이를 Challenge Response라 함
- https://techcommunity.microsoft.com/t5/iis-support-blog/ntlm-want-to-know-how-it-works/ba-p/34784
LogonUI
- LogonUI.exe 프로세스는 Logon 시 Credential 정보를 획득하기 위한 사용자 인터페이스를 제공하는데 사용되는 User-Mode 프로세스
- LogonUI는 Credential Provider를 이용하여, Username/Password, Smartcard, Fingerprint 등 다양한 Logon Credential Input 형태를 제공
- Credential Provider는 LogonUI.exe 프로세스에 DLL로 로드
- Winlogon은 SAS event(Ctrl + Alt + Delete)를 받으면 LogonUI에게 이를 알려 Credential Provider가 제공하는 화면을 표시
- How to debug a Credential Provider locally : https://www.paralint.com/2011/03/how-to-debug-a-credential-provider-locally
Netlogon
- Netlogon(netlogon.dll)은 LSASS 프로세스 Context 내에서 실행 중인 서비스로 Secure Channel을 구현
- Client와 Domain Controller는 preconfigured shared secret(Computer의 Machine Account Password)을 이용하여 계산된 session key를 통해 암호화된 Secure Channel을 통해 통신
- 이 Secure Channel을 통해 Client는 사용자로부터 전달받은 Credential 정보를 Domain Controller에게 안전하게 전달
- Enabling debug logging for the Netlogon service : https://learn.microsoft.com/en-us/troubleshoot/windows-client/windows-security/enable-debug-logging-netlogon-service
Secure Channel 확인 및 복구 방안
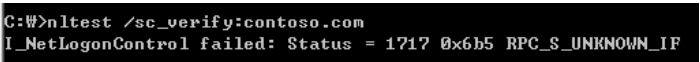
https://glennopedia.com/2016/02/25/how-to-reset-secure-channel-on-a-domain-controller/
To enable Netlogon logging
Open a Command Prompt window (administrative Command Prompt window for Windows Server 2012 R2 and later versions).
Type the following command, and then press Enter:
Nltest /DBFlag:2080FFFF
It's typically unnecessary to stop and restart the Netlogon service for Windows Server 2012 R2 or later to enable Netlogon logging. Netlogon-related activity is logged to %windir%\debug\netlogon.log.
Verify new writes to this log to determine whether a restart of the Netlogon service is necessary.
If you have to restart the service, open a Command Prompt window (administrative Command Prompt window for Windows 10, and Windows Server 2012 R2 and later versions). Then run the following commands:
net stop netlogon
net start netlogon
%windir%\debug\netlogon.log
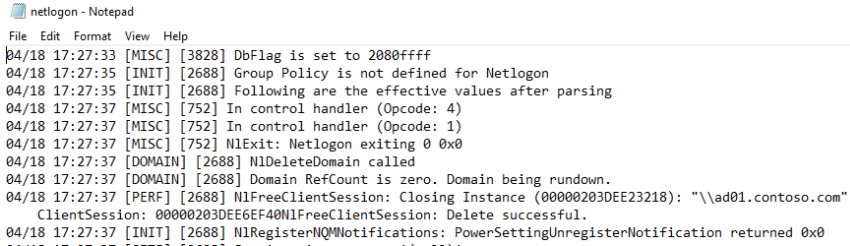
Access Checks
- Access Check는 대부분의 Object에 대해서 수행
- 이를 위해 Security Descriptor를 이용
- Security Descriptor는 Owner의 SID, Group의 SID, DACL, SACL 정보 포함
- Access Check는 Object의 Security Descriptor 정보와 현재 접근을 요청하는 객체의 Security Context 정보를 비교
- https://learn.microsoft.com/en-us/windows/win32/api/winnt/ns-winnt-security_descriptor
SECURITY_DESCRIPTOR
| typedef struct _SECURITY_DESCRIPTOR { BYTE Revision; BYTE Sbz1; SECURITY_DESCRIPTOR_CONTROL Control; PSID Owner; PSID Group; PACL Sacl; PACL Dacl; } SECURITY_DESCRIPTOR, *PISECURITY_DESCRIPTOR; |
- Security Reference Monitor(SRM) 내에서 SeAccessCheck 함수를 이용하여 Access Check
| BOOLEAN SeAccessCheck( [in] PSECURITY_DESCRIPTOR SecurityDescriptor, [in] PSECURITY_SUBJECT_CONTEXT SubjectSecurityContext, [in] BOOLEAN SubjectContextLocked, [in] ACCESS_MASK DesiredAccess, [in] ACCESS_MASK PreviouslyGrantedAccess, [out] PPRIVILEGE_SET *Privileges, [in] PGENERIC_MAPPING GenericMapping, [in] KPROCESSOR_MODE AccessMode, [out] PACCESS_MASK GrantedAccess, [out] PNTSTATUS AccessStatus ); |
- 사용자가 Windows에 Logon 할 때, Security Subsystem은 User와 Group의 SID를 Security Access Token에 설정
- Security Access Token은 모든 Application Process에 부여
- Application이 File, Registry Key등 Object에 접근하려고 할 때마다, Security Subsystem을 통해 접근 가능 여부를 결정
- SRM은 Access Token의 User와 Group SID를 접근하고자 하는 Object의 Security Desriptor내의 접근 권한과 비교
- 만약 User의 SID가 Security Descriptor의 ACL에서 Full Access 권한을 부여받으면, 해당 User가 실행한 Application은 Object에 Full Access가 가능
- https://learn.microsoft.com/en-us/windows-hardware/drivers/debugger/-token
| 6: kd> dt nt!_TOKEN +0x000 TokenSource : _TOKEN_SOURCE +0x010 TokenId : _LUID +0x018 AuthenticationId : _LUID +0x020 ParentTokenId : _LUID +0x028 ExpirationTime : _LARGE_INTEGER +0x030 TokenLock : Ptr64 _ERESOURCE +0x038 ModifiedId : _LUID +0x040 Privileges : _SEP_TOKEN_PRIVILEGES +0x058 AuditPolicy : _SEP_AUDIT_POLICY +0x078 SessionId : Uint4B +0x07c UserAndGroupCount : Uint4B +0x080 RestrictedSidCount : Uint4B +0x084 VariableLength : Uint4B +0x088 DynamicCharged : Uint4B +0x08c DynamicAvailable : Uint4B +0x090 DefaultOwnerIndex : Uint4B +0x098 UserAndGroups : Ptr64 _SID_AND_ATTRIBUTES +0x0a0 RestrictedSids : Ptr64 _SID_AND_ATTRIBUTES +0x0a8 PrimaryGroup : Ptr64 Void +0x0b0 DynamicPart : Ptr64 Uint4B +0x0b8 DefaultDacl : Ptr64 _ACL +0x0c0 TokenType : _TOKEN_TYPE +0x0c4 ImpersonationLevel : _SECURITY_IMPERSONATION_LEVEL +0x0c8 TokenFlags : Uint4B +0x0cc TokenInUse : UChar +0x0d0 IntegrityLevelIndex : Uint4B +0x0d4 MandatoryPolicy : Uint4B +0x0d8 LogonSession : Ptr64 _SEP_LOGON_SESSION_REFERENCES +0x0e0 OriginatingLogonSession : _LUID +0x0e8 SidHash : _SID_AND_ATTRIBUTES_HASH +0x1f8 RestrictedSidHash : _SID_AND_ATTRIBUTES_HASH +0x308 pSecurityAttributes : Ptr64 _AUTHZBASEP_SECURITY_ATTRIBUTES_INFORMATION +0x310 Package : Ptr64 Void +0x318 Capabilities : Ptr64 _SID_AND_ATTRIBUTES +0x320 CapabilityCount : Uint4B +0x328 CapabilitiesHash : _SID_AND_ATTRIBUTES_HASH +0x438 LowboxNumberEntry : Ptr64 _SEP_LOWBOX_NUMBER_ENTRY +0x440 LowboxHandlesEntry : Ptr64 _SEP_CACHED_HANDLES_ENTRY +0x448 pClaimAttributes : Ptr64 _AUTHZBASEP_CLAIM_ATTRIBUTES_COLLECTION +0x450 TrustLevelSid : Ptr64 Void +0x458 TrustLinkedToken : Ptr64 _TOKEN +0x460 IntegrityLevelSidValue : Ptr64 Void +0x468 TokenSidValues : Ptr64 _SEP_SID_VALUES_BLOCK +0x470 IndexEntry : Ptr64 _SEP_LUID_TO_INDEX_MAP_ENTRY +0x478 DiagnosticInfo : Ptr64 _SEP_TOKEN_DIAG_TRACK_ENTRY +0x480 BnoIsolationHandlesEntry : Ptr64 _SEP_CACHED_HANDLES_ENTRY +0x488 SessionObject : Ptr64 Void +0x490 VariablePart : Uint8B 6: kd> !process 0 0 lsass.exe PROCESS ffffd5828c176080 ## <--- SessionId: 0 Cid: 02d4 Peb: e2444d7000 ParentCid: 0228 DirBase: 407237000 ObjectTable: ffffa3076368d9c0 HandleCount: 1080. Image: lsass.exe 6: kd> !process ffffd5828c176080 1 PROCESS ffffd5828c176080 SessionId: 0 Cid: 02d4 Peb: e2444d7000 ParentCid: 0228 DirBase: 407237000 ObjectTable: ffffa3076368d9c0 HandleCount: 1080. Image: lsass.exe VadRoot ffffd5828c9fcb90 Vads 148 Clone 0 Private 1322. Modified 109. Locked 3. DeviceMap ffffa30761a136c0 Token ffffa307653be7f0 ## <--- ElapsedTime 00:00:38.352 UserTime 00:00:00.015 KernelTime 00:00:00.000 QuotaPoolUsage[PagedPool] 121400 QuotaPoolUsage[NonPagedPool] 25384 Working Set Sizes (now,min,max) (3720, 50, 345) (14880KB, 200KB, 1380KB) PeakWorkingSetSize 3664 VirtualSize 2101338 Mb PeakVirtualSize 2101338 Mb PageFaultCount 4170 MemoryPriority BACKGROUND BasePriority 9 CommitCharge 1582 6: kd> !exts.token -n ffffa307653be7f0 _TOKEN 0xffffa307653be7f0 TS Session ID: 0 User: S-1-5-18 (Well Known Group: NT AUTHORITY\SYSTEM) User Groups: 00 S-1-5-32-544 (Alias: BUILTIN\Administrators) Attributes - Default Enabled Owner 01 S-1-1-0 (Well Known Group: localhost\Everyone) Attributes - Mandatory Default Enabled 02 S-1-5-11 (Well Known Group: NT AUTHORITY\Authenticated Users) Attributes - Mandatory Default Enabled 03 S-1-16-16384 (Label: Mandatory Label\System Mandatory Level) Attributes - GroupIntegrity GroupIntegrityEnabled Primary Group: S-1-5-18 (Well Known Group: NT AUTHORITY\SYSTEM) Privs: 02 0x000000002 SeCreateTokenPrivilege Attributes - Enabled 03 0x000000003 SeAssignPrimaryTokenPrivilege Attributes - 04 0x000000004 SeLockMemoryPrivilege Attributes - Enabled Default 05 0x000000005 SeIncreaseQuotaPrivilege Attributes - 07 0x000000007 SeTcbPrivilege Attributes - Enabled Default 08 0x000000008 SeSecurityPrivilege Attributes - 09 0x000000009 SeTakeOwnershipPrivilege Attributes - 10 0x00000000a SeLoadDriverPrivilege Attributes - 11 0x00000000b SeSystemProfilePrivilege Attributes - Enabled Default 12 0x00000000c SeSystemtimePrivilege Attributes - 13 0x00000000d SeProfileSingleProcessPrivilege Attributes - Enabled Default 14 0x00000000e SeIncreaseBasePriorityPrivilege Attributes - Enabled Default 15 0x00000000f SeCreatePagefilePrivilege Attributes - Enabled Default 16 0x000000010 SeCreatePermanentPrivilege Attributes - Enabled Default 17 0x000000011 SeBackupPrivilege Attributes - 18 0x000000012 SeRestorePrivilege Attributes - 19 0x000000013 SeShutdownPrivilege Attributes - 20 0x000000014 SeDebugPrivilege Attributes - Enabled Default 21 0x000000015 SeAuditPrivilege Attributes - Enabled Default 22 0x000000016 SeSystemEnvironmentPrivilege Attributes - 23 0x000000017 SeChangeNotifyPrivilege Attributes - Enabled Default 25 0x000000019 SeUndockPrivilege Attributes - 28 0x00000001c SeManageVolumePrivilege Attributes - 29 0x00000001d SeImpersonatePrivilege Attributes - Enabled Default 30 0x00000001e SeCreateGlobalPrivilege Attributes - Enabled Default 31 0x00000001f SeTrustedCredManAccessPrivilege Attributes - 32 0x000000020 SeRelabelPrivilege Attributes - 33 0x000000021 SeIncreaseWorkingSetPrivilege Attributes - Enabled Default 34 0x000000022 SeTimeZonePrivilege Attributes - Enabled Default 35 0x000000023 SeCreateSymbolicLinkPrivilege Attributes - Enabled Default 36 0x000000024 SeDelegateSessionUserImpersonatePrivilege Attributes - Enabled Default Authentication ID: (0,3e7) Impersonation Level: Anonymous TokenType: Primary ## <--- Source: *SYSTEM* TokenFlags: 0x2000 ( Token in use ) Token ID: 7f39 ParentToken ID: 0 Modified ID: (0, 8b03) RestrictedSidCount: 0 RestrictedSids: 0x0000000000000000 OriginatingLogonSession: 0 PackageSid: (null) CapabilityCount: 0 Capabilities: 0x0000000000000000 LowboxNumberEntry: 0x0000000000000000 Security Attributes: Unable to get the offset of nt!_AUTHZBASEP_SECURITY_ATTRIBUTE.ListLink Process Token TrustLevelSid: (null) |
Security Identifier (SIDs)
- Windows는 User, Group, Computer 같은 Account에 Unique한 SID를 부여
- SID를 이용하여, File / Folder / Database 등과 같은 자원에 대해 Access Check를 수행
- SID는 다음과 같은 형태로 구성 : S-1-5-21-1931071232-1247330687-1096122002-500
- 첫 번째 S-1-5-21은 Windows NT를 의미 : S-1-5-21
- 그 다음 3개 Block은 Windows Domain 또는 Workgroup을 구분 : 1931071232-1247330687-1096122002
- 마지막 숫자가 User 또는 Group을 구분 : 500 ## administrator SID
| C:\Users\Administrator\Downloads\SysinternalsSuite>PsGetsid64.exe /? PsGetSid v1.46 - Translates SIDs to names and vice versa Copyright (C) 1999-2023 Mark Russinovich Sysinternals - www.sysinternals.com Usage: PsGetsid64.exe [\\computer[,computer2[,...] | @file] [-u Username [-p Password]]] [account | SID] -u Specifies optional user name for login to remote computer. -p Specifies optional password for user name. If you omit this you will be prompted to enter a hidden password. account PsGetSid will report the SID for the specified user account rather than the computer. SID PsGetSid will report the account for the specified SID. computer Direct PsGetSid to perform the command on the remote computer or computers specified. If you omit the computer name PsGetSid runs the command on the local system, and if you specify a wildcard (\\*), PsGetSid runs the command on all computers in the current domain. @file PsGetSid will execute the command on each of the computers listed in the file. -nobanner Do not display the startup banner and copyright message. C:\Users\Administrator\Downloads\SysinternalsSuite>PsGetsid64.exe administrator PsGetSid v1.46 - Translates SIDs to names and vice versa Copyright (C) 1999-2023 Mark Russinovich Sysinternals - www.sysinternals.com SID for CONTOSO\administrator: S-1-5-21-1931071232-1247330687-1096122002-500 C:\Users\Administrator\Downloads\SysinternalsSuite>PsGetsid64.exe S-1-5-21-1931071232-1247330687-1096122002-500 PsGetSid v1.46 - Translates SIDs to names and vice versa Copyright (C) 1999-2023 Mark Russinovich Sysinternals - www.sysinternals.com Account for S-1-5-21-1931071232-1247330687-1096122002-500: User: CONTOSO\administrator |
Impersonation and Tokens
- Token은 인증이 정상적으로 완료된 이후에 Logon 과정에서 생성
- 개별 Process와 Thread에서 Token 확인 가능
- Token은 Token이 속한 User Account에 대한 정보(Privilege와 Group Membership 등)를 담고 있음
- Token 종류 : Primary, Impersonation, Restricted, Filtered Admin
- Impersonation Token은 Service Process 내의 Thread가 해당 Process의 Security Context가 아닌 Service를 사용하는 Client의 Security Context로 잠시 사용하는 유형
- https://learn.microsoft.com/en-us/windows/win32/com/impersonation
- Impersonation is the ability of a thread to execute in a security context that is different from the context of the process that owns the thread.
- https://blog.palantir.com/windows-privilege-abuse-auditing-detection-and-defense-3078a403d74e
| Primary tokens function as described and are used to present the default security information for a process or thread. Impersonation allows for a thread to perform an operation using an access token from another user or client. Impersonation tokens are typically used in client/server communication. For example, when a user accesses an SMB file share, the server needs a copy of the user’s token to validate that the user has sufficient permissions. The executing server-side thread includes an impersonation token for the user in addition to the thread’s primary token, and uses the impersonation token to perform access checks for the user’s actions. Restricted tokens (also known as a filtered admin token) are a subset of primary or impersonation tokens that have been modified to control privileges or permissions. Restricted access tokens allow the system to remove privileges, add deny-only access control entries, or perform other access rights changes. Even though the user in question is a local administrator, the unelevated cmd.exe shell carries a token restricted to only a handful of privileges. When elevated to run as administrator, the process carries the user’s primary token with a larger list of privileges: |
Security Descriptor
- Security Descriptor에는 다음과 같은 정보가 포함
- 누가 Object를 소유하고 있는지
- 누가 Object에 접근이 가능한지
- Object에 무엇을 할 수 있는지
- 감사 로그의 수준
- Security Descriptor는 여러 Access Control Entry(ACE)들로 구성되며 이 ACE들로 Access Control List(ACL)을 구성
- Object의 Security Descriptor를 문자로 표현하기 위해 Security Descriptor Definition Language(SDDL)를 사용
- SDDL은 DACL과 SACL로 구성
- DACL은 Discretionary Access Control List로 접근 권한을 결정하고, SACL은 System Access Control List로 감사 정책을 결정
- A DACL identifies users and groups who are allowed or denied access to an object
- SACL defines how access is audited on an object
- SDDL 확인 방법
- SC.EXE 사용
| C:\>sc sdshow schedule D:(A;;CCLCSWLORC;;;AU)(A;;CCLCSWRPDTLOCRRCWDWO;;;BA)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;SY)(A;;CCLCSWLORC;;;BU)S:(AU;FA;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;WD) ## DACL D: (A;;CC LC SW LO RC;;;AU) (A;;CC LC SW RP DT LO CR RC WD WO;;;BA) (A;;CC DC LC SW RP WP DT LO CR SD RC WD WO;;;SY) (A;;CC LC SW LO RC;;;BU) ## SACL S: (AU;FA;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;WD) |
- AccessChk Tool
| C:\Users\Administrator\Downloads\SysinternalsSuite>accesschk.exe -c schedule -l Accesschk v6.15 - Reports effective permissions for securable objects Copyright (C) 2006-2022 Mark Russinovich Sysinternals - www.sysinternals.com schedule DESCRIPTOR FLAGS: [SE_DACL_PRESENT] [SE_SACL_PRESENT] [SE_SELF_RELATIVE] OWNER: NT AUTHORITY\SYSTEM [0] ACCESS_ALLOWED_ACE_TYPE: NT AUTHORITY\Authenticated Users SERVICE_QUERY_STATUS SERVICE_QUERY_CONFIG SERVICE_INTERROGATE SERVICE_ENUMERATE_DEPENDENTS READ_CONTROL [1] ACCESS_ALLOWED_ACE_TYPE: BUILTIN\Administrators SERVICE_QUERY_STATUS SERVICE_QUERY_CONFIG SERVICE_INTERROGATE SERVICE_ENUMERATE_DEPENDENTS SERVICE_PAUSE_CONTINUE SERVICE_START SERVICE_USER_DEFINED_CONTROL READ_CONTROL WRITE_DAC WRITE_OWNER [2] ACCESS_ALLOWED_ACE_TYPE: NT AUTHORITY\SYSTEM SERVICE_ALL_ACCESS [3] ACCESS_ALLOWED_ACE_TYPE: BUILTIN\Users SERVICE_QUERY_STATUS SERVICE_QUERY_CONFIG SERVICE_INTERROGATE SERVICE_ENUMERATE_DEPENDENTS READ_CONTROL SACL: [0] : Everyone [FAILED_ACCESS_ACE_FLAG] SERVICE_ALL_ACCESS C:\Users\Administrator\Downloads\SysinternalsSuite>accesschk.exe -l ./test.txt Accesschk v6.15 - Reports effective permissions for securable objects Copyright (C) 2006-2022 Mark Russinovich Sysinternals - www.sysinternals.com C:\Users\Administrator\Downloads\SysinternalsSuite\test.txt DESCRIPTOR FLAGS: [SE_DACL_PRESENT] [SE_SACL_PRESENT] [SE_SACL_AUTO_INHERITED] [SE_SELF_RELATIVE] OWNER: BUILTIN\Administrators [0] ACCESS_ALLOWED_ACE_TYPE: NT AUTHORITY\SYSTEM FILE_ALL_ACCESS [1] ACCESS_ALLOWED_ACE_TYPE: BUILTIN\Administrators FILE_ALL_ACCESS [2] ACCESS_ALLOWED_ACE_TYPE: CONTOSO\administrator FILE_ALL_ACCESS |
- PsService Tool
| C:\Users\Administrator\Downloads\SysinternalsSuite>psservice security schedule PsService v2.26 - Service information and configuration utility Copyright (C) 2001-2023 Mark Russinovich Sysinternals - www.sysinternals.com SERVICE_NAME: Schedule DISPLAY_NAME: Task Scheduler ACCOUNT: LocalSystem SECURITY: [ALLOW] NT AUTHORITY\Authenticated Users Query status Query Config Interrogate Enumerate Dependents Read Permissions [ALLOW] BUILTIN\Administrators Query status Query Config Interrogate Enumerate Dependents Pause/Resume Start User-Defined Control Read Permissions Change Permissions Change Owner [ALLOW] NT AUTHORITY\SYSTEM All [ALLOW] BUILTIN\Users Query status Query Config Interrogate Enumerate Dependents Read Permissions |
Access Rights and Privileges
- Privilege는 User나 Group에 부여되며, Account가 행할 수 있는 특정 Action을 제한하기 위해서 사용
- User가 Privileged Operation을 수행하면, System은 User의 Access Token을 확인해서 해당 User가 필요한 Privilege를 가지고 있는지 파악
| C:\>whoami /priv PRIVILEGES INFORMATION ---------------------- Privilege Name Description State ========================================= ================================================================== ======== SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled SeMachineAccountPrivilege Add workstations to domain Disabled SeSecurityPrivilege Manage auditing and security log Disabled SeTakeOwnershipPrivilege Take ownership of files or other objects Disabled SeLoadDriverPrivilege Load and unload device drivers Disabled SeSystemProfilePrivilege Profile system performance Disabled SeSystemtimePrivilege Change the system time Disabled SeProfileSingleProcessPrivilege Profile single process Disabled SeIncreaseBasePriorityPrivilege Increase scheduling priority Disabled SeCreatePagefilePrivilege Create a pagefile Disabled SeBackupPrivilege Back up files and directories Disabled SeRestorePrivilege Restore files and directories Disabled SeShutdownPrivilege Shut down the system Disabled SeDebugPrivilege Debug programs Disabled SeSystemEnvironmentPrivilege Modify firmware environment values Disabled SeChangeNotifyPrivilege Bypass traverse checking Enabled SeRemoteShutdownPrivilege Force shutdown from a remote system Disabled SeUndockPrivilege Remove computer from docking station Disabled SeEnableDelegationPrivilege Enable computer and user accounts to be trusted for delegation Disabled SeManageVolumePrivilege Perform volume maintenance tasks Disabled SeImpersonatePrivilege Impersonate a client after authentication Enabled SeCreateGlobalPrivilege Create global objects Enabled SeIncreaseWorkingSetPrivilege Increase a process working set Disabled SeTimeZonePrivilege Change the time zone Disabled SeCreateSymbolicLinkPrivilege Create symbolic links Disabled SeDelegateSessionUserImpersonatePrivilege Obtain an impersonation token for another user in the same session Disabled |
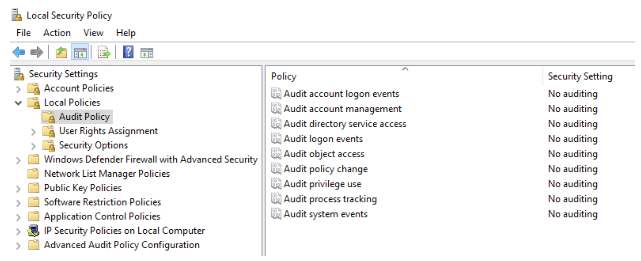
Security Auditing
- Object의 Security Descriptor에는 System Access Control List(SACL)이 있어서 SACL 에 포함된 Access Control Entry(ACE)에 따라 감사 로그를 남길 수 있음
- https://learn.microsoft.com/en-us/windows/security/threat-protection/security-policy-settings/audit-policy
- Audit account logon events
- Audit account management
- Audit directory service access
- Audit logon events
- Audit object access
- Audit policy change
- Audit privilege use
- Audit process tracking
- Audit system events
감사 정책 접근 경로
- 시작 > 실행 > secpol.msc
- 시작 > 실행 > gpedit.msc (Local Group Policy Editor)
- DC의 경우, 서버 관리자 > 도구 > GPMC
Logon
User Logon
https://techcommunity.microsoft.com/t5/itops-talk-blog/deep-dive-logging-on-to-windows/ba-p/2420705
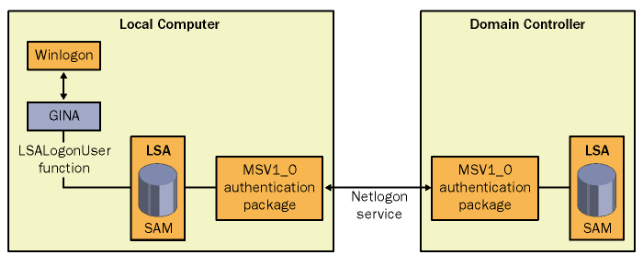
Winlogon
- Winlogon은 사용자 logon/logoff 및 lock/unlock 을 처리
- Winlogon은 Logon 시에 Password 입력을 위해 LogonUI.exe 프로세스를 생성
- Winlogon 프로세스가 LogonUI.exe 를 통해 획득한 Credential을 Lsass.exe 프로세스에게 전달하면서 사용자 인증 요청
- Winlogon 프로세스는 System 중요 프로세스로 예기치 않게 종료될 시 Bugcheck 발생